Hi there! Searching the internet is impossible now, and all good content is locked up behind paywalls or subscriptions, so I’m releasing this freely. You can edit it if you want to in Acrobat or a similar PDF editing app.…
Category: Uncategorized
Welcome to the EFF Benefit Poker Tournament at Defcon 32!
Welcome! Here’s some info as we get ready to play! Nota bene: If you haven’t registered by now, please do so! I need to tell the poker room the expected number of players so they can allocate the correct number of…
“Parental Units–we need to have The Talk.”
Your cost for incident response for a true breach of multiple family member passwords to all financial accounts is going to be a devastating, months-long trauma for them and for you, as you work to not only help them, but must cope with their feelings of frustration and fear. It’s an *awful* IR scenario. We have been mostly fortunate to escape that so far, but I know some friends who have waited just a bit too long to start training family on how to handle online security and have seen finances, relationships, and futures irreparably damaged. This is important, but often gets backburnered. Start making the time now while you have trust and a bit of time.
a process for large meal cooking
I cook at a kitchen for our unhoused neighbors every month, and often am hit with last minute ingredient substitutions, donations of odd ingredients, and interesting food safety questions. Here are some rules for cooking more than 150 meals at…
“Yes, but how do I submit a comment on how unintuitive the comment submission process is?”
I’m smashblogging on a Saturday because I came across this story on FedScoop: https://fedscoop.com/white-house-launches-public-consultation-on-critical-ai-issues/ which discusses the Biden Administration’s Office of Science and Technology Policy’s launch of a public request for comment on their upcoming AI policy work. I wanted…
“If you can’t do something smart, do something right.”
Shepherd Book said that in Serenity, a lovely movie from 2005 that wrapped up the sadly-too-soon cancelled series Firefly. I use it a lot when institutional constraints and incentives stop me from doing the smartest and most effective thing possible.…
What is Montana, anyway?
I talked to a reporter yesterday about the recent TikTok ban legislation passed there, and explained some of the technical difficulties with enforcing any such ban. Hell, even the legislators themselves admit they can’t operationalize and enforce the ban. So,…
Troubleshooting Apple’s iCloud Advanced Data Protection
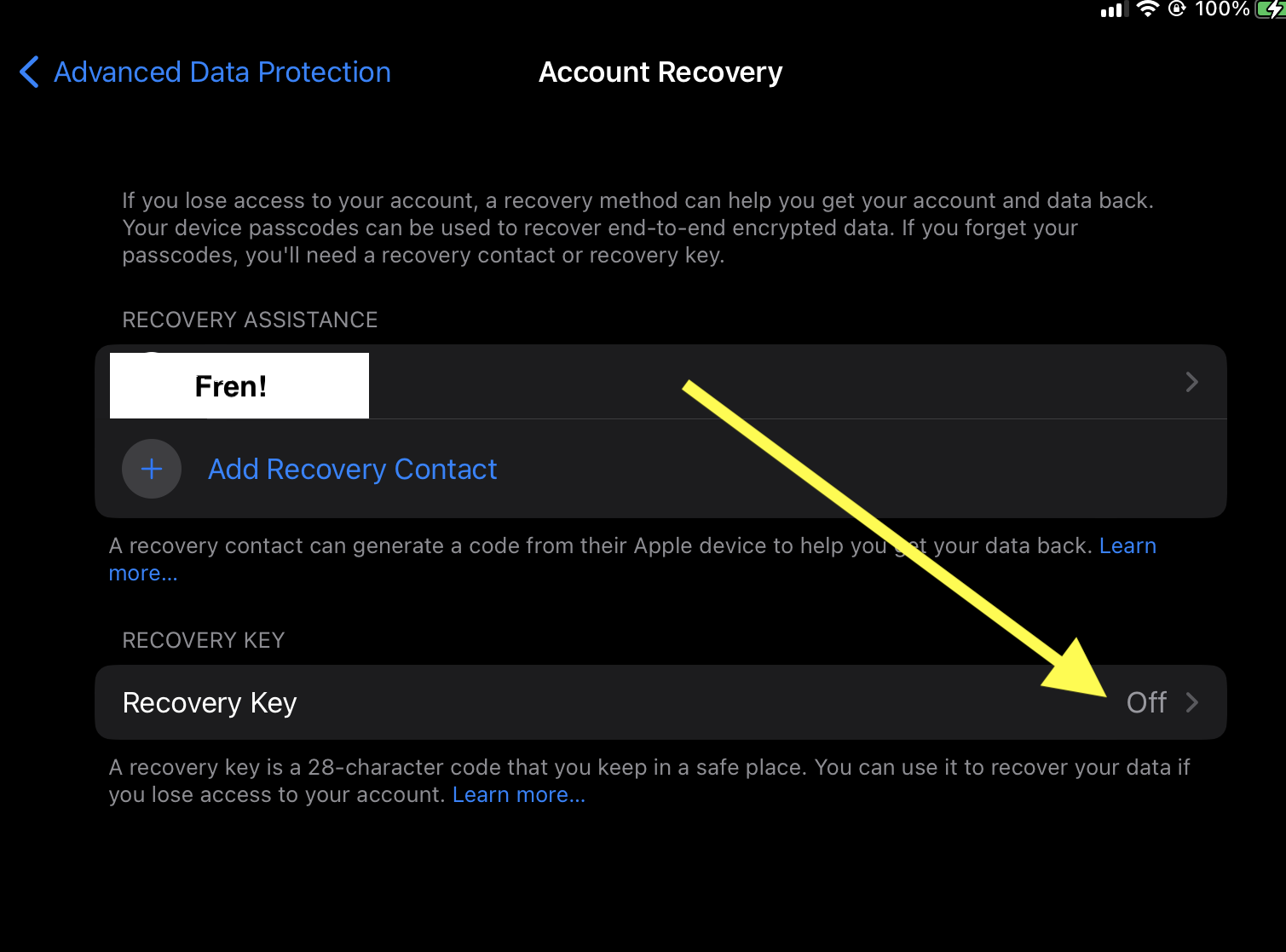
TL;DR: set your recovery key and contact, pick an iCloud device (I used my phone), log fully out of iCloud, and log back in. Try enabling ADP then. I tried a month ago to enable ADP on my iCloud account,…
That’s a nice cyber you’ve got there. Shame if something were to happen to it.
It should deeply concern us that cyber insurance is becoming less available. The CEO of Zurich Insurance (the company that denied Mondelez’s USD 100m claim after NotPetya on the grounds of it being warfare) says “What will become uninsurable is…
Contempt is the most dangerous emotion
There is an entire world of small and mid-sized businesses that are absolutely helpless in front of the kinds of attacks that we call “basic” in infosec. Invoice spearphishing, BEC, credential harvesting – these are the kinds of things we…